58 KiB
- 总复习2023t1 {{renderer :todomaster}}
- DONE Java {{renderer :todomaster}}
collapsed:: true
SCHEDULED: <2023-06-12 Mon>
:LOGBOOK:
CLOCK: [2023-06-09 Fri 15:09:23]--[2023-06-09 Fri 16:26:51] => 01:17:28
:END:
- DONE lab
- DONE 写 lab8 :LOGBOOK: CLOCK: [2023-06-09 Fri 15:06:46]--[2023-06-09 Fri 16:26:50] => 01:20:04 :END:
- DONE (考前)复习 labs
collapsed:: true
- DONE [#A] 从 t14 复制过来
- 1 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- 2 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- 3 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- 4 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- 5 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- 6 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- 7 :LOGBOOK: CLOCK: [2023-06-10 Sat 21:08:02]--[2023-06-10 Sat 21:08:03] => 00:00:01 :END:
- DONE 课件
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-12 Mon 10:47:42]--[2023-06-12 Mon 14:12:02] => 03:24:20
:END:
- DONE 看 revision (java file IO 可以考前再看一遍)
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-12 Mon 11:40:14]--[2023-06-12 Mon 12:58:33] => 01:18:19
:END:
- DONE [#A] Review past exam papers
- DONE java file IO
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-09 Fri 16:44:33]--[2023-06-09 Fri 17:13:37] => 00:29:04
:END:
- DONE Buffered Reader / Writer
- DONE File objects
- DONE GUI (自学不考)
collapsed:: true
- DONE Graphics Classes: Color, Font, FontMetrics, JLabel
- StringBuffer vs. StringBuilder
- String is immutable whereas StringBuffer and StringBuilder are mutable classes.
- StringBuffer is thread-safe and synchronized whereas StringBuilder is not. That’s why StringBuilder is faster than StringBuffer.
- String concatenation operator (+) internally uses StringBuffer or StringBuilder class.
- For String manipulations in a non-multi threaded environment, we should use StringBuilder else use StringBuffer class.
- DONE 看 revision (java file IO 可以考前再看一遍)
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-12 Mon 11:40:14]--[2023-06-12 Mon 12:58:33] => 01:18:19
:END:
- DONE 题
- DONE 看 qm 上错题 gradeplus
- DONE this 的用法
collapsed:: true
- In Java, the
thiskeyword is a reference to the current object within a non-static method or constructor. It represents the instance of the class on which the method or constructor is being called. - When a class is instantiated to create an object, that object has its own set of instance variables and methods. The
thiskeyword allows you to refer to those instance variables and methods from within the class itself. It is primarily used to differentiate between instance variables and parameters or local variables that have the same name. - Here are a few common uses of the
thiskeyword in Java: collapsed:: true- Accessing instance variables: You can use
thisto access or modify the instance variables of the current object. For example,this.variableNamerefers to the instance variablevariableNameof the current object. - Invoking constructors: In a constructor,
thiscan be used to invoke another constructor in the same class. It is useful for constructor chaining, where one constructor calls another constructor to initialize the object. - Passing the current object as a parameter: Sometimes, you may need to pass the current object as an argument to another method. In such cases, you can use
thisto pass a reference to the current object. - Returning the current object: A method can use
thisto return the current object. This is often used in method chaining, where multiple method calls are chained together on the same object.
- Accessing instance variables: You can use
- It's important to note that
thiscan only be used within non-static contexts, as it refers to the current instance of the class. Static methods and variables do not belong to any specific instance, sothiscannot be used inside them. - Overall, the
thiskeyword provides a way to refer to the current object and access its members, helping to avoid naming conflicts and make the code more readable.
- In Java, the
- DONE Past exam papers
:LOGBOOK:
CLOCK: [2023-06-11 Sun 21:37:16]--[2023-06-12 Mon 12:58:29] => 15:21:13
CLOCK: [2023-06-12 Mon 14:12:05]--[2023-06-12 Mon 17:55:24] => 03:43:19
:END:
- DONE Access Modifiers
- DONE Javadoc tags and modifiers tutorial
- Syntax:
-
// This is a single line comment /* * This is a regular multi-line comment */ /** * This is a Javadoc */
-
- @throws ExceptionType reason
- Syntax:
- DONE Garbage collection
collapsed:: true
- The working: Java garbage collection is an automatic process. Automatic garbage collection is the process of looking at heap memory, identifying which objects are in use and which are not, and deleting the unused objects. An in-use object, or a referenced object, means that some part of your program still maintains a pointer to that object. An unused or unreferenced object is no longer referenced by any part of your program. So the memory used by an unreferenced object can be reclaimed. The programmer does not need to mark objects to be deleted explicitly. The garbage collection implementation lives in the JVM.
- Eligibility for garbage collection: An object is said to be eligible for GC(garbage collection) if it is unreachable.
- DONE ==THREE main concepts when doing GUI programming in Java==
- Component: An object that the user can see on the screen and can also interact with
- Container: A component that can hold other components
- Event: An action triggered by the user
- Designing a GUI involves creating components, putting them into containers, and arranging for the program to respond to events (e.g. responding to mouse clicks).
- DONE ==Review Java File IO==
- DONE Exception Terms
- java.lang.ArrayIndexOutOfBoundsException:
- IOException
- ArithmeticException
- NegativeArraySizeException
- ArrayStoreException
- LATER four fundamental OOP concepts.
:LOGBOOK:
CLOCK: [2023-06-12 Mon 14:12:16]--[2023-06-12 Mon 14:12:18] => 00:00:02
:END:
- inheritance
- Inheritance in Java is a concept that acquires the properties from one class to other classes
-
polymorphism
- encapsulation
- Encapsulation in Java is a mechanism of wrapping the data (variables) and code acting on the data (methods) together as a single unit. In encapsulation, the variables of a class will be hidden from other classes, and can be accessed only through the methods of their current class. Therefore, it is also known as data hiding.
- abstraction.
- Data abstraction is the process of hiding certain details and showing only essential information to the user.
- Abstraction can be achieved with either abstract classes or interfaces (which you will learn more about in the next chapter).
- inheritance
- Overloading vs. overriding
- When two or more methods in the same class have the same method name but different parameters, this is called overloading. In contrast, overriding occurs when two methods have the same name and parameters
- Interface
- DONE lab
- DONE 毛概 {{renderer :todomaster}}
collapsed:: true
SCHEDULED: <2023-06-13 Tue>
- DONE 看笔记
- DONE 做题 :LOGBOOK: CLOCK: [2023-06-11 Sun 09:51:00]--[2023-06-11 Sun 09:51:01] => 00:00:01 :END:
- DONE 整理错题
deck:: 2023t1/Mao
- 在 1978 年的关于真理标准问题的⼤讨论中,邓⼩平指出,关于真理标准问题的讨论实质就在于( {{c1 b}} ). #flashcard id:: 64895ec0-db81-4923-8c25-48429b1b0999 A.是否坚持⻢列主义、⽑泽东思想 B.是否坚持实践是==检验真理==的唯⼀标准 C.是否坚持解放思想、实事求是 D.是否坚持中国共产党的领导
- 创新包括各⽅⾯的创新,如理论创新、技术创新、制度创新等,其中在各项创新中处于先导地位的是 ( {{c1 b}})#flashcard extra:: 社会主义主打一个空想 id:: 64895ec0-eb6a-4252-9bb6-89eff3bc6e76 A.科技创新 B.理论创新 C.⽂化创新 D.⽣产关系创新 A.⽣产关系适合⽣产⼒ B.理论联系实际 C.实事求是 D.在实践中检验真理和发展真理
- extra:: 三个有利于:改革得失 A.尊重群众、尊重实践 B.⼀切从群众中来 C.解放思想 D.“三个有利于”
- 4.中国共产党在新⺠主主义⾰命领导权问题上有着深刻认识,党认为实现对⾰命的领导权的根本 id:: 64895ec0-a0c3-4205-9240-3bbea356fab0 保证是( {{c1 c}} )。 #flashcard A.动员全⺠开展武装⽃争 B.建⽴最⼴泛的⼈⺠统⼀战线 C.加强中国共产党的建设 D.扩⼤⾰命的影响⼒和控制⼒
- extra:: a: 抢国民党
id:: 64895ec0-f849-4a5c-8fe9-d3deb0e3fdcb
- 建国初期我国社会主义国营经济建⽴的主要途径是( {{c1 a}} )#flashcard A. 没收官僚资本 B. 没收帝国主义在华企业 C. 剥夺封建地主阶级的财产 D. 赎买⺠族资产阶级的财产
- extra:: 学苏联 A.优先发展重⼯业的问题 B.将落后的农业国建设成为先进的⼯业国的问题 C.重⼯业、轻⼯业和农业的发展关系问题 D.建⽴独⽴的⽐较完整的⼯业体系问题
- extra:: b 反右运动 c 文革 d 从来没有 A.集中⼒量发展社会⽣产⼒ B.正确处理⼈⺠内部⽭盾 C.进⾏思想战线上的社会主义⾰命 D.加强社会主义⺠主与法制建设
- extra:: 创新性方法:学苏联自由派 A.和平赎买 B.剥夺⽣产资料 C.公私合营 D.⽣活上给出路
- extra:: 十大关系指出要多快好省建设社会主义基本思想 A.发展⽣产⼒,把我国尽快地从落后的农业国变为先进的⼯业国 B.正确处理⽆产阶级同资产阶级的⽭盾 C.调动⼀切积极因素,为社会主义事业服务 D.彻底消灭剥削制度,继续肃清反⾰命残余势⼒
- 1.社会主义的根本原则是( {{c1 a}} ) #flashcard extra:: 根本原则 id:: 64895ec0-3dc2-4451-a8fe-24381236c3fd A. 坚持以公有制为主体,实现共同富裕 B.扩⼤改⾰开放,增强综合国⼒ C.实⾏按劳分配,改善⼈⺠⽣活 D. 不断发展⽣产,增加社会财富 是( {{c1 d}} ) #flashcard A.什么是实事求是 B. 怎样建设党 C.什么是⻢克思主义 D. 什么是社会主义
- 5.坚持四项基本原则的核⼼是 ( {{c1 c}} ) #flashcard extra:: 共产党要独裁,别人都不行 id:: 64895ec0-9e79-4649-93be-cf27f0fc42ba A.坚持社会主义道路 B.坚持⼈⺠⺠主专政 C.坚持共产党的领导 D.坚持⻢列主义、⽑泽东思想
- 3.社会主义初级阶段与新⺠主主义社会在经济基础⽅⾯的本质区别在于( {{c1 a}} )#flashcard extra:: d: 不谈这些 id:: 64895ec0-7ac9-4e1d-bb5b-ce5ee51f4897 A. 是否存在多种所有制经济 B. ⾮公有制经济是否成为社会主义经济的必要补充 C. 国有经济是否起主导作⽤ D. 公有制经济是否成为社会经济的主体
- 2.正确处理改⾰、发展、稳定三者关系的重要结合点是( {{c1 b}} )#flashcard id:: 64895ec0-d70c-4c98-94bb-80fcbe503533 A.把改⾰的⼒度、发展的速度和社会可以承受的程度统⼀结合起来 B.不断改善⼈⺠⽣活 C.在社会政治稳定中推进改⾰和发展 D.靠深化和继续发展解决改⾰和发展中产⽣的新问题和新⽭盾
- 5.经过 30 多年的对外开放,我国形成了全⽅位、多层次、宽领域的对外开放格局。所谓全⽅位就是 指( {c1 a})#flashcard extra:: 全方位:a; 多层次:合作框架, 宽领域:跨越政治 id:: 64895ec0-0a5a-4f41-a262-adbb511a9af6 A.不论对资本主义国家还是社会主义国家,对发达国家还是发展中国家都实⾏开放政策 B. 根据各地区的实际和特点,通过经济特区、沿海开放城市、经济技术开发区等不同开放程度的 各种形式,形成全国范围的对外开放 C.⽴⾜我国国情,对国际商品市场、国际资本市场、国际技术市场和国际劳务市场的开放 D. 坚持“引进来”和“⾛出去”相结合
- 1.我国现阶段公有制的主要实现形式是( {{c1 a}} )#flashcard extra:: b: 农村银行 id:: 64895ec0-a04c-4640-a3a9-e1dd807a7745 A. 股份制 B.股份合作制 C.租赁、承包制 D.国家独资经济 A.国有资产在社会总资产中占有量的优势 B.国有经济能控制垄断性⾏业 C.国有经济对国⺠经济的==控制⼒== D.国有经济在国⺠经济中占主体地位
- 是( {{c1 b}} ) #flashcard extra:: 领导利益优先 id:: 64895ec0-a755-4622-9044-19bef1cbc32e A.维护最⼴⼤⼈⺠的根本利益 B.如何妥善协调各⽅⾯的利益关系问题 C.兼顾不同⽅⾯群众的利益 D.效率优先、兼顾公平
- 1.新⺠主主义⾰命初期,⽑泽东⽐较了中外资产阶级⾰命的性质后,提出中国⾰命胜利后,应该建⽴的国家政权形式是 ( {{c1 b}} ). #flashcard extra:: 共产党约等于革命民众 id:: 64895ec0-8194-401b-9372-ecb960a032eb A. ⼈⺠⺠主专政的国家 B. 各⾰命⺠众合作统治的国家 C. ⺠主联合政府的国家 D. 以⼯农为主的⼯农⺠主政权
- 2.中国共产党和各⺠主党派合作的政治基础是 ( {{c1 c}} ). #flashcard extra:: 四项基本原则不允许争议,指“社会主义”,“民主”,“共产党独裁”,“马列毛思想”不允许反对 id:: 64895ec0-3678-4873-adfd-82b4df53da19 A. 中国共产党和各⺠主党派全作的政治基础是 B. 遵循“⻓期共存,互相监督,肝胆相照,荣辱与共”的⽅针 C. 坚持四项基本原则 D. 中国共产党是执政党,⺠主党派是参政党
- 5.社会主义⺠主政治的本质是 ( {{c1 a}} ). #flashcard extra:: 红二代当家作主最重要 id:: 64895ec0-da3e-46f8-92ab-c0da5efe157e A. ⼈⺠当家作主 B. ⼈⺠⺠主专政 C. ⼈⺠代表⼤会制度 D. ⼈⺠参与国家管理
- A. 爱国主义
extra:: 共产党最爱吹的金句
id:: 64895ec0-dd09-45f4-a3d4-073860b4dd0b
B. 集体主义
C. 社会主义
D. 为⼈⺠服务
A. 为⼈⺠服务
B. 集体主义
C 诚实可信
D 爱国主义
- 社会主义和谐社会的核⼼价值是( {{c1 d}} ). #flashcard A. 以⼈为本 B. 以⺠为本 C 社会公平 D 公平和正义
- 2 我国社会保障制度的基本⽬标是( {{c1 a}} ). #flashcard extra:: 竟然是和其他所有国家一样 id:: 64895ec0-8e70-4ef1-81a7-5cd033cfac67 A. 保证⼈们最基本的⽣活需要 B. 使劳动者⽣活⽔平不断提⾼ C. 保证劳动者充分就业 D. 实现共同富裕
- extra:: A. 不断推进⼈的全⾯发展 B. 不断推进共同富裕 C. 不断满⾜⼈⺠的物质⽂化⽣活需要 D. 不断创造共同富裕的物质基础
- A. 祖国统⼀
extra:: 因为是假想敌,所以想要统一
id:: 64895ec0-11d5-40f6-84d9-dc9fef824774
B. ⼀国两制
C. ⼀国两政府
D. “三通”
- 和平与发展是时代的主题,和平与发展的核⼼问题是( {{c1 a}} ). #flashcard A. 南北问题 B. .维护世界和平问题 C. 反对霸权主义、强权政治问题 D. 建⽴国际经济政治新秩序问题 A. 提⾼中国的国际地位 B. 维护世界和平,促进⼈类共同繁荣和发展 C. 反对霸权主义和强权政治 D. 实现全⼈类的解放
- extra:: 是全球的南北
id:: 64895ec0-83fb-4abe-9f80-566a43e15750
- 和平与发展是时代的主题,和平与发展的核⼼问题是( {{c1 a}} ). #flashcard A. 南北问题 B. .维护世界和平问题 C. 反对霸权主义、强权政治问题 D. 建⽴国际经济政治新秩序问题
- extra:: 美国=霸权主义,反对美国来维护世界和平 A. 实⾏有效裁军和军控 B. 发挥联合国的维和作⽤ C. 反对霸权主义和强权政治 D. 加强国际⼲预
- extra:: 民族资产阶级最后被收购了
id:: 64895ec0-83af-4a8b-9fb9-805f7ec7d617
- 中国新⺠主主义⾰命时期的统⼀战线包含着两个联盟。其中基本的、主要的联盟是( {{c1 b}} ). #flashcard A. ⼯⼈阶级同城市⼩资产阶级的联盟 B. 以⼯农联盟为主体的⼯⼈阶级同农⺠、⼩资产阶级等其他劳动⼈⺠的联盟 C. 以⼯农联盟为主体的⼯⼈阶级同农⺠、⼩资产阶级和⺠族资产阶级的联盟 D. ⼯⼈阶级同可以合作的⾮劳动⼈⺠的联盟
- extra:: 共产党你是会恶心人的 A. 爱国主义性质的 B. 政治联盟性质的 C. 社会主义性质的 D. ⼈⺠⺠主性质的
- extra:: 硬背吧 A. 建设有中国特⾊社会主义 B. 实现国家统⼀ C. 加强⺠族团结 D. 增强⼈⺠凝聚⼒
- extra:: 重点是体制
id:: 64895ec0-21ac-4215-9fd7-63c4fff95559
- ⼗六届四中全会指出,提⾼党的执政能⼒的核⼼是( {{c1 d}} ). #flashcard A. 加强党的领导 B. 改善党的领导体制 C. 建设⾼素质的⼲部队伍 D. 保持党和⼈⺠群众的⾎⾁关系
- extra:: 共产党纯变态 A. 政党是阶级⽃争发展到⼀定历史阶段的产物 B. 政党同国家政权紧密联系 C. 政党有⾃⼰的纲领 D. 政党有⾃⼰的奋⽃⽬标 A. 取得执政地位 B. 代表先进⽣产⽅式 C. 维护⽆产阶级利益 D. 符合统治阶级的需要
- DONE 学交 {{renderer :todomaster}}
collapsed:: true
SCHEDULED: <2023-06-13 Tue>
- DONE 看格式要求 Follow the ABC (Abstract Body Conclusion) Format for all Letters/Memos
- DONE Job application letter
- Cover letter (application letter)
-
#+BEGIN_VERSE [Your name] [Your address] [Your city, state and zip code]
[Date] [Hiring manager's name] [Hiring manager's title] [Company name] [Company address] [Company city, state and zip code] Dear [Hiring manager's name], I'm writing to express my interest in the position of [job title] at [company]. [Explain how you heard about the job and name your contact if you were referred by someone within the company.] I believe my [skills and qualifications] make me an ideal fit for this job. [Use the second paragraph to elaborate on how you would help the company. Reference specific campaigns or projects when possible.] [Use the third paragraph to summarize your key qualifications. Elaborate on your most important accomplishments and include details that you were unable to provide in the more concise format of your resume.] [Use the fourth paragraph to briefly explain why you want to work for this company. Mention the additional documents included with your cover letter, and express your excitement about moving forward in the hiring process.] Sincerely, [Your name]#+END_VERSE
-
- Cover letter (application letter)
- DONE Academic
- DONE research proposal
- Format
-
#+BEGIN_VERSE Your proposal should include the following:
-
TITLE
Your title should give a clear indication of your proposed research approach or key question
-
BACKGROUND AND RATIONALE
You should include:
the background and issues of your proposed research identify your discipline a short literature review a summary of key debates and developments in the field- RESEARCH QUESTION(S)
You should formulate these clearly, giving an explanation as to what problems and issues are to be explored and why they are worth exploring
- RESEARCH METHODOLOGY
You should provide an outline of:
the theoretical resources to be drawn on the research approach (theoretical framework) the research methods appropriate for the proposed research a discussion of advantages as well as limits of particular approaches and methods- PLAN OF WORK & TIME SCHEDULE
You should include an outline of the various stages and corresponding time lines for developing and implementing the research, including writing up your thesis.
For full-time study your research should be completed within three years, with writing up completed in the fourth year of registration.
For part-time study your research should be completed within six years, with writing up completed by the eighth year.
- BIBLIOGRAPHY
You should include:
a list of references to key articles and texts discussed within your research proposal a selection of sources appropriate to the proposed research#+END_VERSE
-
-
- Format
- DONE academic paper
- DONE abstract
- Major Types of Abstract - Descriptive Abstracts
- ● Short -uaually less than 120 words.
- ● Includes:
- ● purpose of the paper/work (objectives)
- ● methods used
- ● scope of the paper/work
- ● introducing the subject.
- ● Doesn’t include:
- ● results, conclusions and recommendations
- It aims to provide the reader with brief summaries (1-2 sentences) of each of the sections of the paper.
- ● A descriptive abstract summarizes the main points of a document without providing any analysis or interpretation, simply describing what the document contains. It is typically very short and doesn't provide any information beyond what you would find in the document's table of contents.
- ● An outline of your work
- •Major Types of Abstract - Informative Abstracts
- ● Fairly short - from 250 words to a page or more.
- ● Include:
- ● purpose of the work/paper (research background /objectives)
- ● method used
- ● scope of the work
- ● results / findings
- ● conclusions and recommendations
- ● contributions, novelty (optional)
- It focuses on providing the results of the research and describing the conclusion, contribution and vovelty that can be drawn from these results.
- Major Types of Abstract - Descriptive Abstracts
- DONE introduction
- a clear sense of purpose, thorough understanding of reader needs, and close attention to correct formats.
- Research paper introductions are always unique. After all, research is original by definition. However, they often contain six essential items. These are:
- **An overview of the topic.**Start with a general overview of your topic. Narrow the overview until you address your paper’s specific subject. Then, mention questions or concerns you had about the case. Note that you will address them in the publication.
- **Prior research.**Your introduction is the place to review other conclusions on your topic. Include both older scholars and modern scholars. This background information shows that you are aware of prior research. It also introduces past findings to those who might not have that expertise.
- **A rationale for your paper.**Explain why your topic needs to be addressed right now. If applicable, connect it to current issues. Additionally, you can show a problem with former theories or reveal a gap in current research. No matter how you do it, a good rationale will interest your readers and demonstrate why they must read the rest of your paper.
- **Describe the methodology you used.**Recount your processes to make your paper more credible. Lay out your goal and the questions you will address. Reveal how you conducted research and describe how you measured results. Moreover, explain why you made key choices.
- **A thesis statement.**Your main introduction should end with a thesis statement. This statement summarizes the ideas that will run through your entire research article. It should be straightforward and clear.
- **An outline.**Introductions often conclude with an outline. Your layout should quickly review what you intend to cover in the following sections. Think of it as a roadmap, guiding your reader to the end of your paper.
- These six items are emphasized more or less, depending on your field. For example, a physics research paper might emphasize methodology. An English journal article might highlight the overview.
- DONE conclusion
- Presenting the last word on the issues you raised in your paper.
- Summarizing your thoughts and conveying the larger implications of your study.
- Demonstrating the importance of your ideas.
- Introducing possible new or expanded ways of thinking about the research problem.
- DONE abstract
- DONE research proposal
- DONE Report
- Informal
- DONE letter report
- Format
-
#+BEGIN_VERSE This form is used in the case of brief and informal reports. Its main parts are:
Heading; Date; Address; Salutation; Body; Complimentary close; Signature.The body of the letter can be divided into the following parts:
Introduction: Here the writer states the problem. Findings: Here the finding of the investigation are presented. Recommendation: After the findings, recommendations are given in the last paragraph of the body.The sample is given below to give an idea about the structure of a report. #+END_VERSE
-
- Sample
-
Opex Apparel Ltd. (A house for best Garments) Dhanmondi, Dhaka 25th, May 2021 Managing Director Opex Apparel Ltd. Dhanmondi, Dhaka. Ref: Negligence of duty by the staff in our Uttara Showroom. Dear Sir, In accordance with” your instructions, I personally visited our Uttara showroom to look into its functioning. I made some investigation and therefore submitting my report hereunder. <abstract, introduction> A number of worthy customers purchased some exclusive garments but found some problems with fitting after purchase. They tried their best to return the garments but failed because there was no attendant to take the complaint and providing the change. As a result, they made a phone call to our complaint department and filed complaints regarding this issue. <findings> In our Uttara branch, there is only one attendant named Mr. Saker to handle the after-sales service. He has been found to be irregular for the last three (3) months. As a result, our customers are getting dissatisfaction causing a decrease in our sales. In this age of competition, losing customers means “Red Alert to the business. I have no hesitation to recommend that Mr. Saker may be served with a notice and a really efficient and active man may be sent there for proper functioning. <recommendation> I hope that quick action will be taken based on my recommendation for the betterment of our company.<close> Yours faithfully M. A Khan Secretary
-
- Format
- DONE memo report
- Format
- Abstract
- Clear statement of memo's purpose Outline of main parts of memo
- Body
- Supporting points, with strong points at the beginning and/or end Frequent use of short paragraphs or listed items Absolute clarity about what memo has to do with reader Tactful presentation of any negative news
- Conclusion
- Clear statement of what step should occur next Another effort to retain goodwill and cooperation of readers
- Abstract
- Sample:
-
MEMORANDUM DATE: TO: FROM: SUBJECT: I'm writing to inform you that [statement, reason for writing memo]. As our company continues to grow … [evidence or reason to support your opening paragraph]. Please let me know if you have any questions. In the meantime, I'd appreciate your cooperation as [official business information] takes place.
-
- Format
- DONE letter report
- Formal
- DONE Letter Text Combination Form
- Types
- proposal: A proposal report is a document that outlines a plan or suggestion for a particular project, initiative, or course of action. It is typically prepared by an individual or a team who wants to propose a specific idea, action, or solution to a problem. The purpose of a proposal report is to convince the intended audience that the proposed plan is viable, beneficial, and worth pursuing.
- feasibility: A feasibility report determines the outcome of a proposed solution by analyzing all relevant factors.
- progress: A progress report is a document that provides an update on the status, achievements, and ongoing activities of a project, task, or initiative. It is typically prepared on a regular basis, such as weekly, monthly, or quarterly, to inform stakeholders about the progress made toward established goals and objectives.
- evaluation: An evaluation report is a document that assesses and analyzes the performance, effectiveness, or impact of a project, program, policy, or initiative. It provides an in-depth examination and critique of the subject being evaluated, based on specific criteria and objectives.
- problem analysis: A problem analysis report is a document that examines and analyzes a specific problem or issue in depth. It aims to identify the root causes of the problem, understand its impact, and propose potential solutions or recommendations.
- recommendation: Recommendation reports, also known as justification reports, propose a specific idea to the reader and provide evidence to support the recommendation.
- Template
-
Report on [topic of the report] Submitted on [date of submission] Summary or Abstract [This summarizes the contents of the report, including your main findings and overall conclusion.] Introduction [This provides insight into the purpose of the report.] Background [This section provides background information for the reader to understand the context of the remaining content.] Methodology [This section explains to the reader what method you followed to gather your findings and make your conclusions. For example, describe if you're using qualitative or quantitative methods in your research.] Findings [Present your findings based on your research.] Conclusions The main issues we found were as follows: [Outline the main issues to address based on your findings.] Recommendations To address these central issues, we recommend the following steps: [Offer clear recommendations of actions based on your findings and conclusions to help solve the problem.] Appendix [List any references used for your research, including articles, papers, or other sources. You can also include any reference materials, such as surveys, tables, charts, or diagrams referenced in your report.]
-
- Types
- DONE Letter Text Combination Form
- Informal
- DONE Job application letter
- LATER 写几篇试试手
- DONE 看格式要求 Follow the ABC (Abstract Body Conclusion) Format for all Letters/Memos
- DONE 数电 {{renderer :todomaster}}
SCHEDULED: <2023-06-14 Wed>
deck:: 2023t1/Circuits
collapsed:: true
- DONE 看 block4
deck:: 2023t1/Circuits
- Buses #flashcard what is it? connection types?
id:: 64895ec0-bc6b-4db5-b6a9-ce4cd728dd78
- Set of two or more electrical conductors representing a binary value
- Often more than just a one-to-one connection
- Data Storage Devices
- Random Access: #flashcard Access parallel? Access time? address length? two categories of random access?
id:: 64895ec0-0708-4f9d-b106-24296716fa8d
- All memory contents can be accessed in the same time as each other.
- Equal time to access any location
- n-bit address
- Volatile #flashcard: content lost? also called? two types?
id:: 64895ec0-ee26-4729-aaa3-56f824aa8d43
- Volatile memory loses its contents when the power is switched off
- Volatile memory is commonly called {{c1 RAM(Random Access Memory)}}. Often used as “working id:: 64895ec0-3638-4913-98ab-53cea78b5f2a memory” #flashcard
- Static RAM (SRAM): Uses {{c3 transistors}} to store a single bit
id:: 64895ec0-f8f6-4e99-8557-db4f6b38b40a
of information and does not need to be refreshed
periodically. #flashcard
- more expensive and less dense
- Dynamic RAM (DRAM)Uses a {{c2 capacitor}} to store the
id:: 64895ec0-dd35-4cf8-b386-5a244312a79b
data bit and needs to be periodically refreshed to maintain
the charge in the capacitors. #flashcard
- Because of the small cell size, DRAM can have very high densities.
- It is the main memory in personal computers.
- Non-volatile #flashcard data loss? abbrevation?
id:: 64895ec0-aad5-47f6-84a6-543ea7d930a5
- Non-volatile memory keeps its contents even if there is no power to the device.
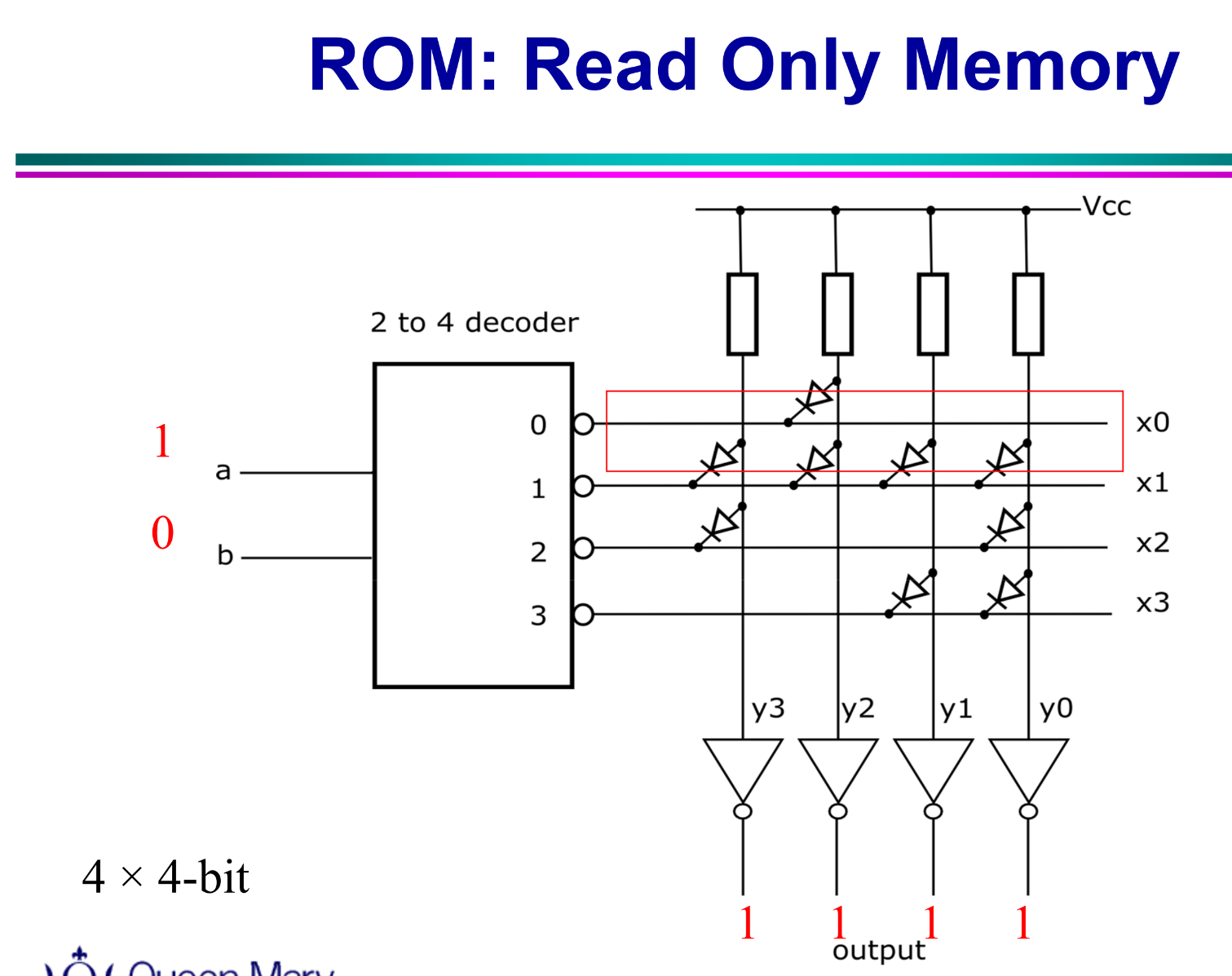
- Non-volatile memory is commonly called as {{c1 ROM}} id:: 64895ec0-e7ff-4a6c-bb06-731bb9f26413
- ROM
- Definition :-> Read-Only Memory where the contents cannot be id:: 64895ec0-0b10-47d5-9a55-d86e9d711777 changed by normal CPU operations.
- used to store fixed data or information.
- Mask ROM :-> programmed in manufacture id:: 64895ec0-665d-48e3-9c6f-8d98d499fb44
- PROM :-> Programmable ROM id:: 64895ec0-7ad7-4186-a070-46403fa1adbd
- EPROM :-> Erasable PROM id:: 64895ec0-d5d4-4888-8c51-0cc852162e81
- EEPROM :-> Electrically Erasable PROM id:: 64895ec0-82fd-4910-8365-bbcb7ec7b089
- Serial Access
- Stores data bits in series Head must travel from current position to new address passing the other addresses in between – time consuming Can store large amounts of data
- Read Only
- R / W
- Random Access: #flashcard Access parallel? Access time? address length? two categories of random access?
id:: 64895ec0-0708-4f9d-b106-24296716fa8d
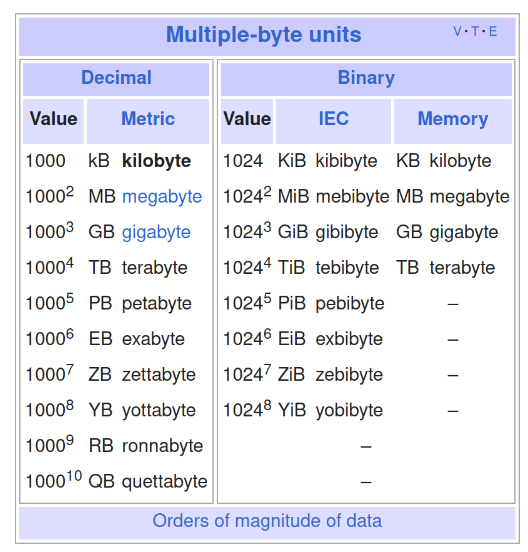
- SI bytes:
8bit = 1byte
- Buses #flashcard what is it? connection types?
id:: 64895ec0-bc6b-4db5-b6a9-ce4cd728dd78
- DONE 往年题
- DONE Review slides
:LOGBOOK:
CLOCK: [2023-06-11 Sun 20:05:19]--[2023-06-11 Sun 21:37:27] => 01:32:08
:END:
- DONE Tutorial 1
:LOGBOOK:
CLOCK: [2023-06-11 Sun 20:06:12]--[2023-06-11 Sun 21:13:20] => 01:07:08
:END:
- DONE Base conversion
- Integer
- Digits
- If calculating integer part, from up to down :-> LSB to MSB id:: 64895ec0-d31b-4520-9651-c06319d4fca2
- fractional part is the reverse, :-> from MSB to LSB, since we are multiplying. id:: 64895ec0-eb02-4a85-b47c-e55ec4ff9e63
- DONE LSB, MSB
- DONE ==2's complement==
:LOGBOOK:
CLOCK: [2023-06-11 Sun 20:24:32]
CLOCK: [2023-06-11 Sun 20:24:34]--[2023-06-11 Sun 20:32:57] => 00:08:23
:END:
- convert to 2's complement (negative numbers)
- Invert the bits of that representation logseq.order-list-type:: number
- add 1 logseq.order-list-type:: number
- convert from 2's complement (negative numbers)
- subtract 1 logseq.order-list-type:: number
- invert the bits of that representation logseq.order-list-type:: number
- or:
- invert bits logseq.order-list-type:: number
- add 1 logseq.order-list-type:: number
- Subtraction with 2's complement
- convert to 2's complement (negative numbers)
- DONE Floating point formats
:LOGBOOK:
CLOCK: [2023-06-11 Sun 20:53:09]--[2023-06-11 Sun 21:09:13] => 00:16:04
:END:
- IEEE 754 FP
-
Value = (-1)^s _ 1.f _ 2^{e-127} - s: sign
- f: Mantissa
- e: exponent
-
- IEEE 754 FP
- Parity
- DONE Base conversion
- DONE Tutorial 2
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-13 Tue 19:02:54]--[2023-06-13 Tue 19:53:03] => 00:50:09
:END:
- Drawing gates
- Boolean algebra
- Theorems
- Consensus theorem
-
(X + Y) (X + Z) = X + YZ
-
- Distributivity theorem
-
XY + X'Z + YZ = XY + X'Z
-
- Consensus theorem
- Theorems
- Minterms and Maxterms
- Minterm
- Algebraic sum of minterms, SOP, Canonical Sum
- Algebraic product of maxterms, POS, Canonical Product
- Minterm
- DONE Tutorial 3
:LOGBOOK:
CLOCK: [2023-06-13 Tue 19:56:43]--[2023-06-13 Tue 20:31:16] => 00:34:33
:END:
- Draw latches
- SR
- SR with control
- D
- Draw Functional table
- DONE When the output is invalid
- Synchronous state machine
- Input / next state / output equations
- Transition table, State table, State / Output Table
- Circuit synthesis
- K-map
- State diagram
- Draw latches
- DONE Tutorial 4
:LOGBOOK:
CLOCK: [2023-06-13 Tue 20:36:09]--[2023-06-13 Tue 21:21:19] => 00:45:10
:END:
- Calculating address bits
- Calculating bits required to select memory chips
- draw diagrams
- DONE Draw block diagram of circuit using decoder so that memory can be addrerssed
:LOGBOOK:
CLOCK: [2023-06-13 Tue 21:33:12]--[2023-06-13 Tue 21:33:12] => 00:00:00
:END:
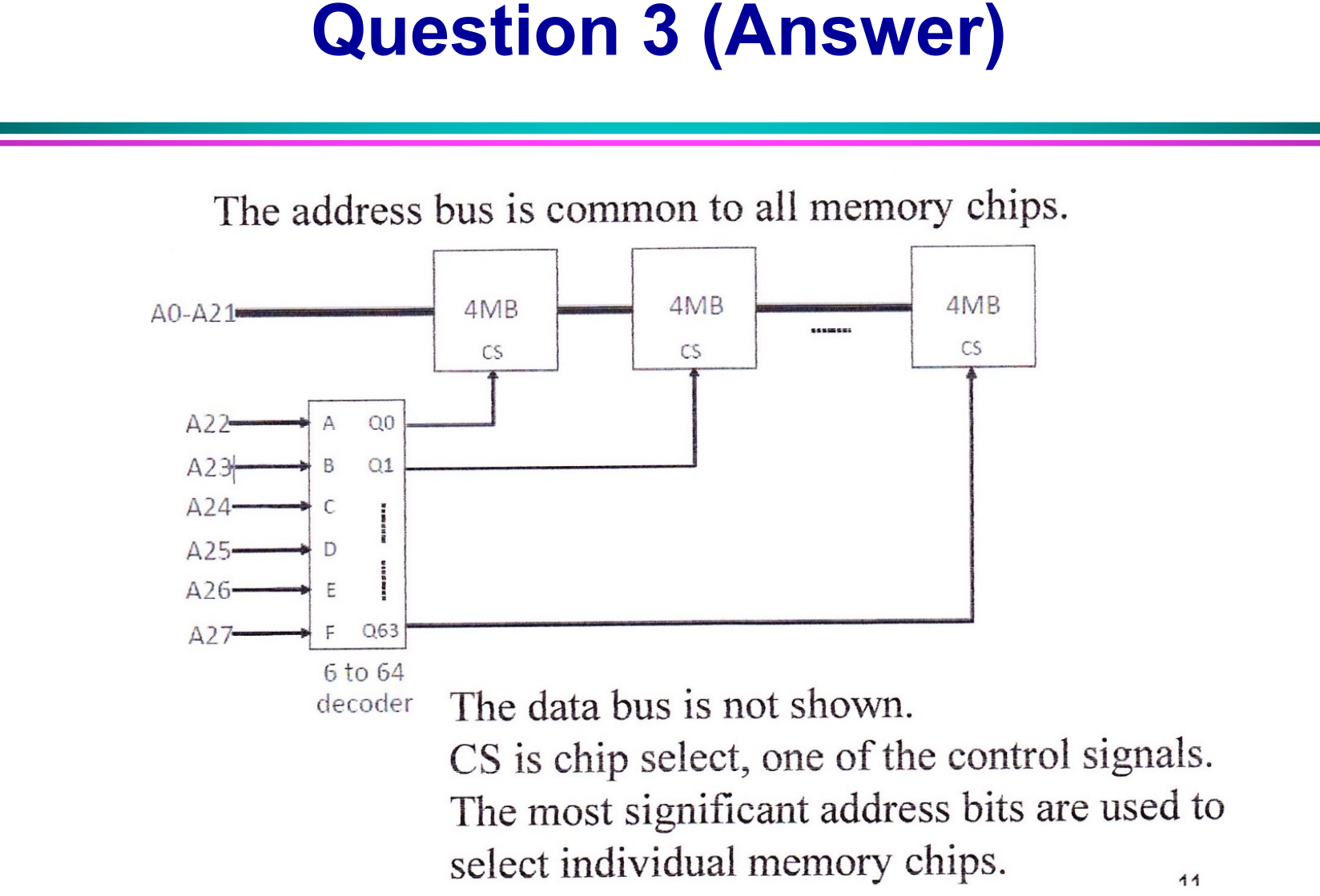
- DONE Draw block diagram of a system in which a memory space comprises multiple memory devices of smaller capacity and explain its operation :LOGBOOK: CLOCK: [2023-06-13 Tue 21:33:12]--[2023-06-13 Tue 21:33:12] => 00:00:00 :END:
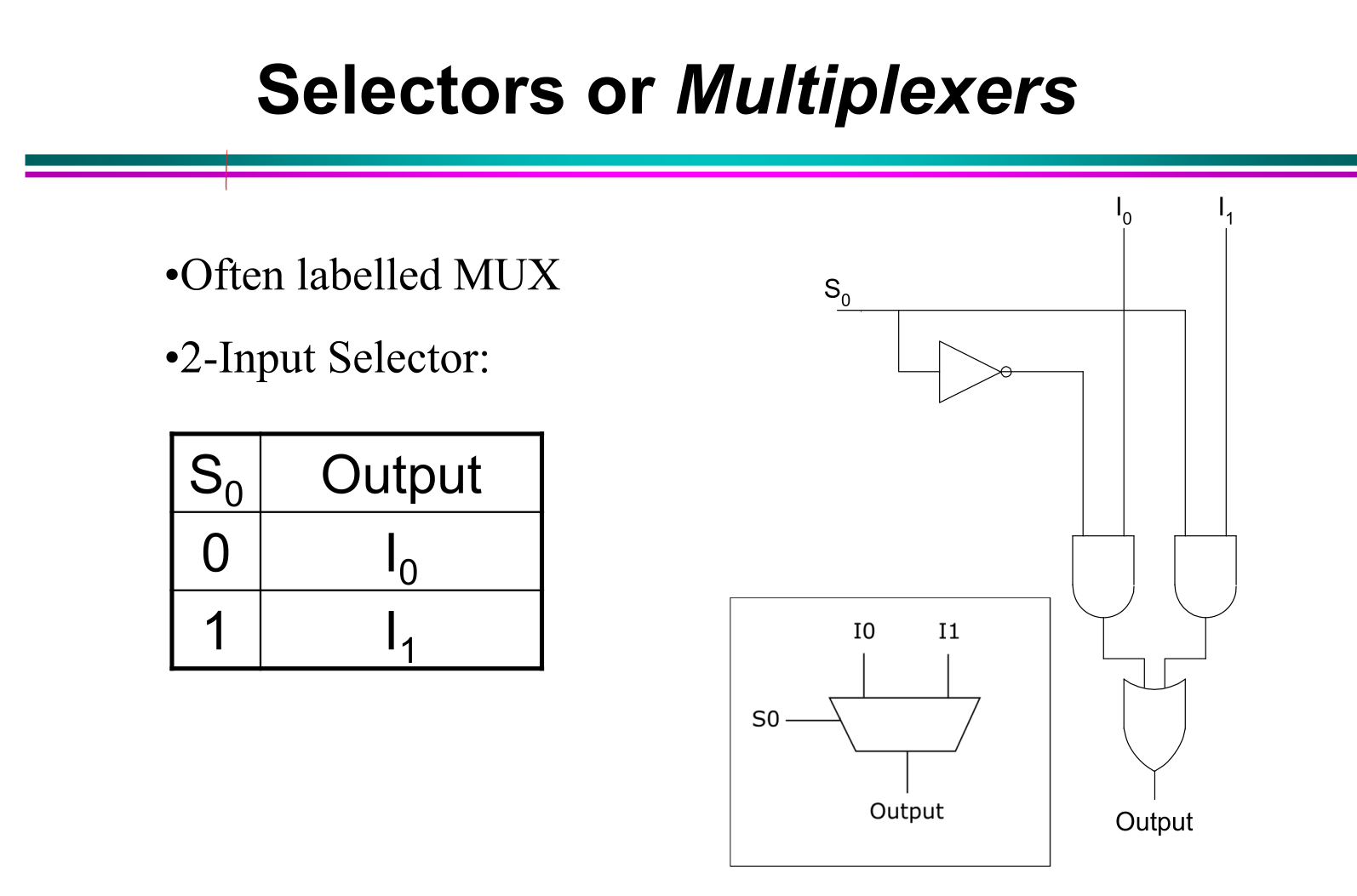
- DONE Mux switch
:LOGBOOK:
CLOCK: [2023-06-13 Tue 21:33:12]--[2023-06-13 Tue 21:33:12] => 00:00:00
:END:
- DONE Draw ROM
:LOGBOOK:
CLOCK: [2023-06-13 Tue 21:33:12]--[2023-06-13 Tue 21:33:12] => 00:00:00
:END:
 The address is from b to a (down to up):
c b a addr
0 0 0 0
0 0 1 1
0 1 0 2
0 1 1 3
==mux switch left 1, right 0==
The address is from b to a (down to up):
c b a addr
0 0 0 0
0 0 1 1
0 1 0 2
0 1 1 3
==mux switch left 1, right 0== - DONE Ripple parallel adder implemented by FAs
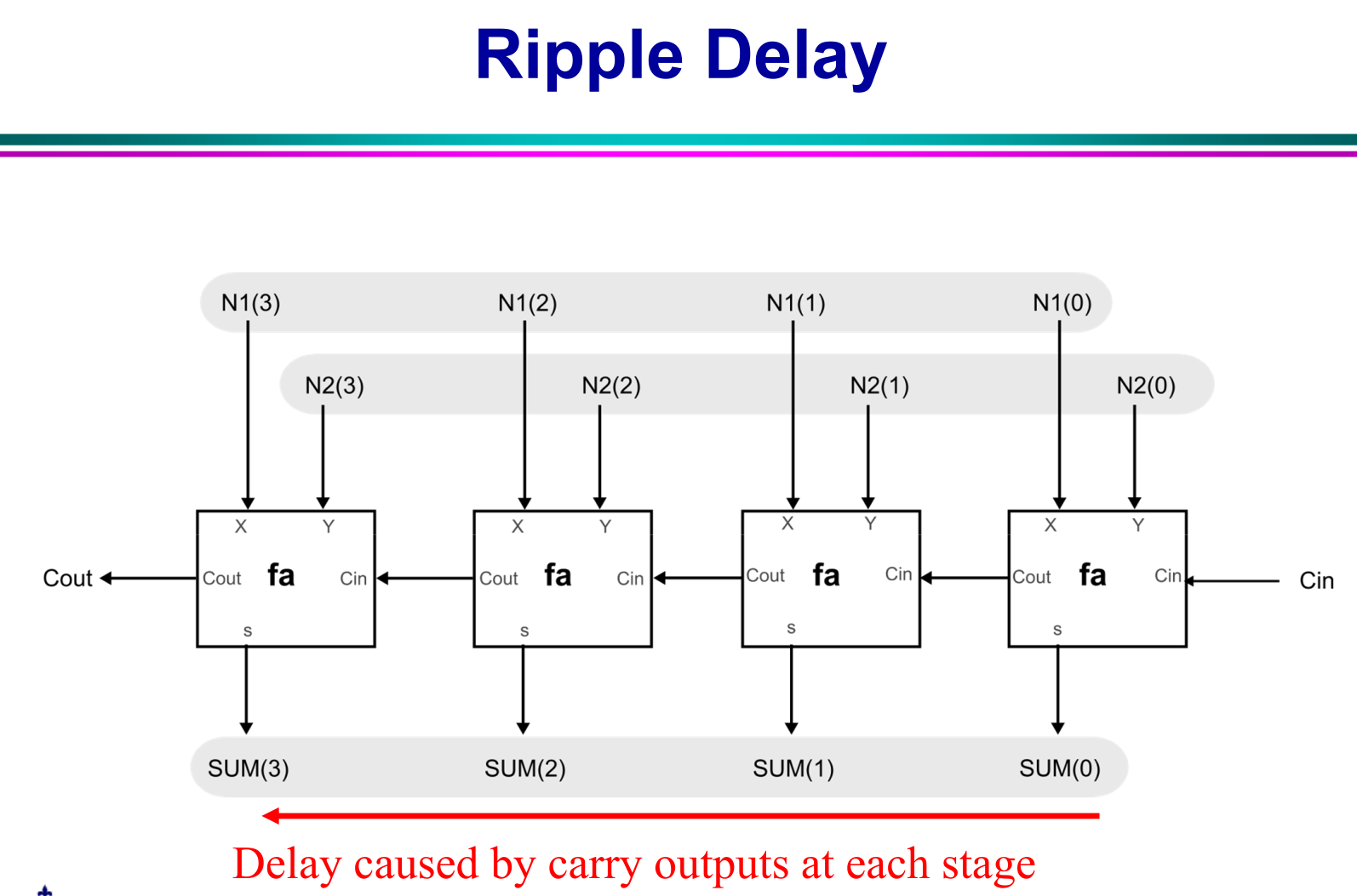
- DONE Ripple parallel subtractor implemented by FAs
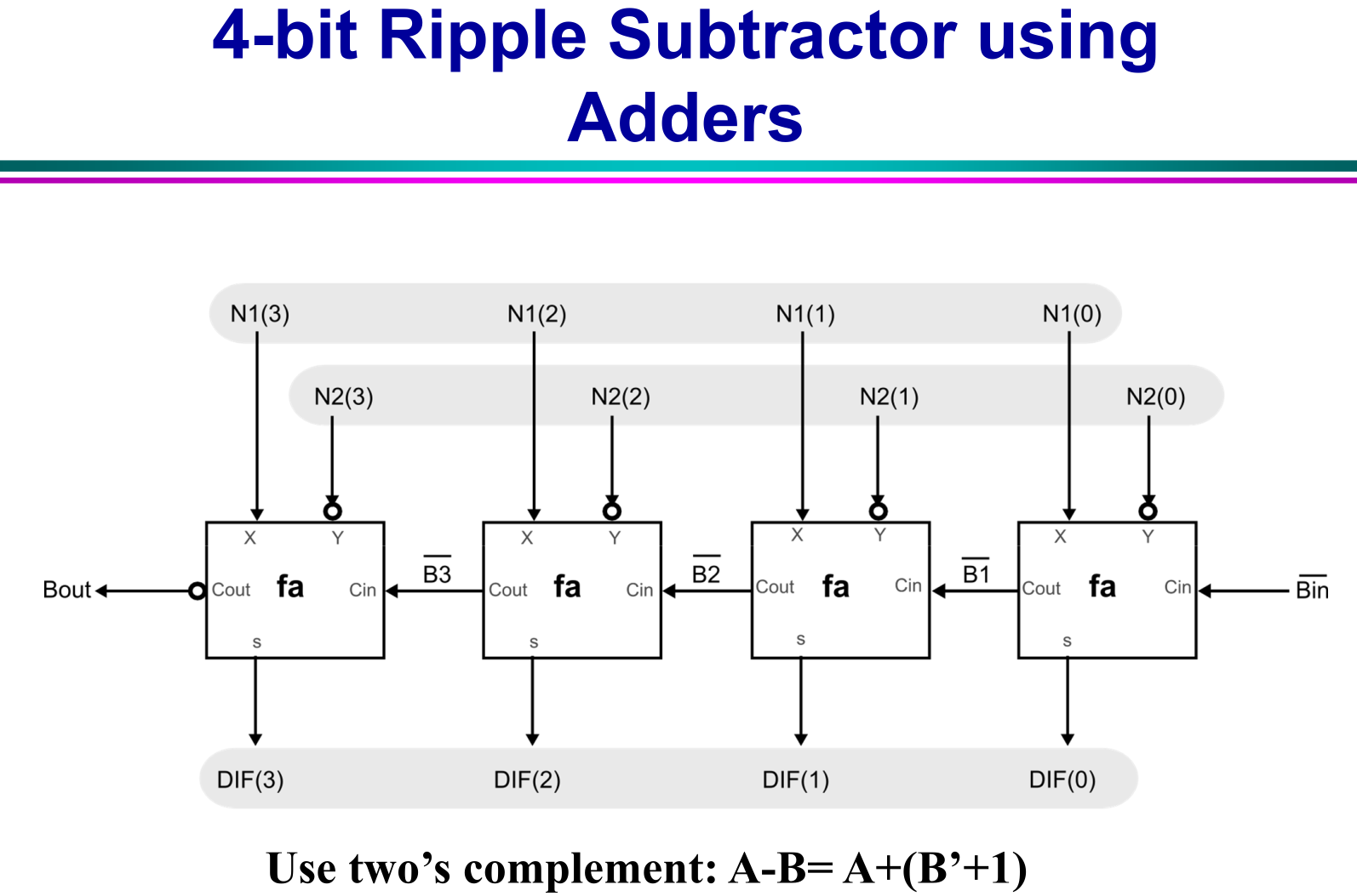
- DONE Draw block diagram of circuit using decoder so that memory can be addrerssed
:LOGBOOK:
CLOCK: [2023-06-13 Tue 21:33:12]--[2023-06-13 Tue 21:33:12] => 00:00:00
:END:
- Transforming bit, byte, kb, mb, gb
- DONE Tutorial 1
:LOGBOOK:
CLOCK: [2023-06-11 Sun 20:06:12]--[2023-06-11 Sun 21:13:20] => 01:07:08
:END:
- DONE 看 block4
deck:: 2023t1/Circuits
- LATER 看数据库 {{renderer :todomaster}}
deck:: 2023t1/database
- DONE 课件
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-01 Thu 17:01:28]--[2023-06-01 Thu 17:01:30] => 00:00:02
CLOCK: [2023-06-01 Thu 17:01:41]--[2023-06-01 Thu 17:38:19] => 00:36:38
:END:
- DONE Transactions
- DONE Distributed DMBSs
- DONE XML
- DONE Data Mining
- DONE NoSQL
- LATER Theory
:LOGBOOK:
CLOCK: [2023-06-04 Sun 16:27:23]--[2023-06-04 Sun 16:54:55] => 00:27:32
:END:
- LATER Block 1
- DONE DBMS
- Database is :-> a shared collection of logically related data (and a description of this data), designed to meet the information needs of an organization. id:: 64895ec0-d724-4159-a95d-657afd171c29
- Table :-> A collection of related data organized into rows (also called records) and columns (also called fields). id:: 64895ec0-2290-4f62-8711-45e99803c82e
- Row/Record :-> A single set of data in a table, representing a specific instance or entity. id:: 64895ec0-12a9-402d-8c1d-64c40e169bb2
- Column/Field :-> A specific attribute or data element within a table. id:: 64895ec0-2aed-4aa8-a34f-446fd7715db6
- Primary Key :-> A unique identifier for each row/record in a table. It ensures the integrity and uniqueness of the data. id:: 64895ec0-7339-477c-b765-b12fd18e9df4
- Foreign Key :-> A field in one table that refers to the primary key in another table, establishing a relationship between the two tables. id:: 64895ec0-75e5-4378-aa9c-b4af6d7d37c9
- Relationship :-> The connection between tables based on common data values, such as primary and foreign keys. id:: 64895ec0-ab80-4eed-bb91-0911b1954368
- Normalization :-> The process of organizing and structuring a database design to eliminate redundancy and improve data integrity. id:: 64895ec0-8b79-4172-8cad-25e4edada659
- Index :-> A data structure that improves the retrieval speed of data from a database table by creating a quick reference to the location of the data. id:: 64895ec0-f3cd-4625-b2ca-6e94f870b34d
- Query :-> A request for data or information from a database, usually written using Structured Query Language (SQL). id:: 64895ec0-df79-46a4-8fb2-09b34a414c9c
- SQL (Structured Query Language) :-> A programming language used to manage and manipulate relational databases. It allows you to create, modify, and retrieve data from databases. id:: 64895ec0-4de4-4cfd-8042-7f92458a8a26
- CRUD Operations :-> An acronym for Create, Read, Update, and Delete operations, which are the basic operations used to manage data in a database. id:: 64895ec0-77ed-4253-947e-2a54c4235a05
- ACID (Atomicity, Consistency, Isolation, Durability) :-> A set of properties that guarantee the reliability and integrity of database transactions. id:: 64895ec0-e18b-4340-8a24-98b2cbaec1fd
- Data Integrity :-> The accuracy, consistency, and reliability of data stored in a database. id:: 64895ec0-023b-47dc-96bd-7a4c52fd9717
- Database Schema :-> The structure or blueprint of a database, defining the tables, fields, relationships, and constraints. id:: 64895ec0-0c9b-49fc-923d-264841105690
- Database Management System (DBMS) :-> Software that provides an interface to interact with databases, managing their creation, modification, and retrieval. id:: 64895ec0-60c1-468f-bc13-bd65c736a682
- DONE basic concepts of Relational model
- A data model :- > a graphical description of the components of database.
- A relation, is :-> a two-dimensional table arranged in columns and rows. id:: 64895ec0-a8ef-4e61-8e31-ce2b319a459b
- A relational database is :-> a collection of relations. id:: 64895ec0-4f99-4abd-a0f1-a0707ff20bd7
- Candidate Key #flashcard
id:: 64895ec0-44d2-4816-9201-492149a1e26e
- A set of attributes that uniquely identifies a tuple within a relation.
- Uniqueness : In each tuple, candidate key uniquely identify that tuple.
- Irreducibility: No proper subset of the candidate key has the uniqueness property.
- Primary Key #flashcard
id:: 64895ec0-057c-49f6-8fd9-0fc599e49e0a
- Candidate key selected to identify tuples uniquely within relation.
- Foreign Key #flashcard
id:: 64895ec0-2bf4-4bf5-92f3-b266cfcce167
- Attribute, or set of attributes, within one relation that matches candidate key of some (possibly same) relation.
- Composite Key #flashcard
id:: 64895ec0-7b2e-4031-97ca-157c1864ac1c
- A candidate key that consists of two or more attributes.
- Recursive Relationship #flashcard
id:: 64895ec0-96f6-4a17-8d67-ddd8c7679066
- Relationship type where same entity type participates more than once in different roles.
- Multiplicity :-> number (or range) of possible
id:: 64895ec0-3514-4e82-acf6-f25238116bb7
occurrences of an entity type that may relate to a
single occurrence of an associated entity type
through a particular relationship.
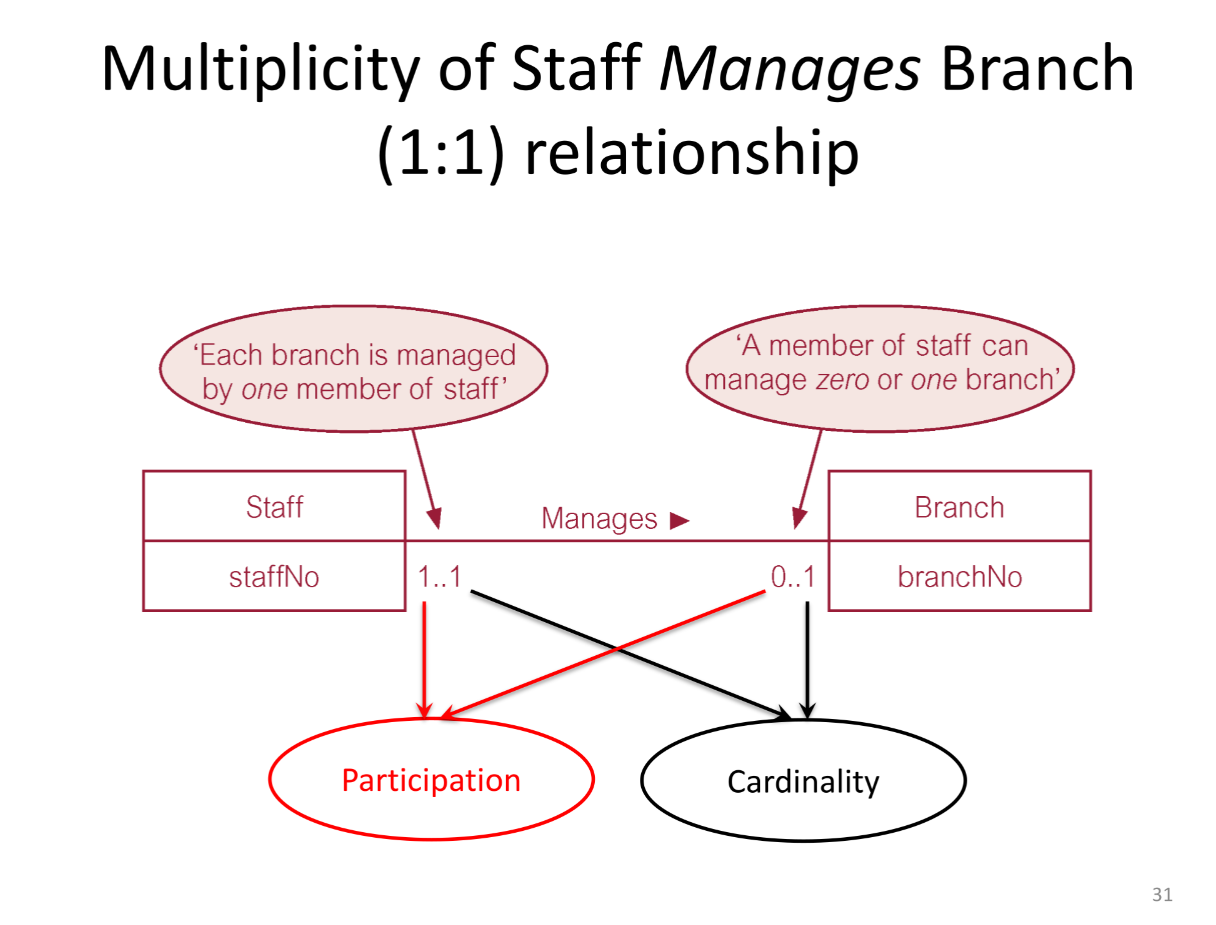
- Cardinality #flashcard
id:: 64895ec0-4ad7-43f2-80fc-489bc0a07ec1
- Describes {{c1 maximum}} number of possible relationship occurrences for an entity participating in a given relationship type. id:: 64895ec0-e8d2-47e1-97b8-d81ed8d62f64
- Participation #flashcard
id:: 64895ec0-c4c3-400e-9cb6-08f722328773
- Determines whether all or only some entity occurrences participate in a relationship.
- Gives the minimum number for an entity occurrences participating in a given relationship type.
- Ternary relationship #flashcard
id:: 64895ec0-0897-4857-b763-0349ae186d62
- a ternary relationship is not the same as three binary relationships!
- Cardinality #flashcard
id:: 64895ec0-4ad7-43f2-80fc-489bc0a07ec1
- LATER basic concepts associated with Entity-Relationship(ER) model.
- LATER Forming sql queries
collapsed:: true
- DONE Review relational algebra https://www.geeksforgeeks.org/introduction-of-relational-algebra-in-dbms/
- LATER review lab2
- LATER SQL join
- DONE DBMS
- LATER Block 2
- LATER EER
- Most useful additional concept of EER model:
specialization/generalization.
- Superclass :-> An entity type that includes one or more distinct
subgroupings of its occurrences.
- Superclass/subclass relationship is one-to-one (1:1).
- Superclass may contain overlapping or distinct subclasses. • Not all members of a superclass need be a member of a subclass.
- Subclass :-> A distinct subgrouping of occurrences of an entity type.
- Superclass :-> An entity type that includes one or more distinct
subgroupings of its occurrences.
- Most useful additional concept of EER model:
specialization/generalization.
- LATER designing ER diagram
- LATER EER
- DONE Block 3
collapsed:: true
- DONE DB transaction management
- DONE ACID (Atomicity, Consistency, Isolation, Durability): A set of properties that guarantee the reliability and integrity of database transactions.
- Atomicity: The property that ensures a transaction is treated as a single, indivisible unit of work. It either executes all its operations successfully or rolls back to the initial state if any operation fails.
- Consistency: The property that ensures a transaction transforms the database from one consistent state to another consistent state. It maintains data integrity and adheres to defined business rules.
- Isolation: The property that ensures concurrent transactions do not interfere with each other. Each transaction operates in isolation until it completes, preventing interference or conflicts.
- Durability: The property that ensures committed changes made by a transaction are permanently saved and will survive any subsequent system failures or crashes.
- DONE Concurrency control
- DONE Meaning of serialisability.
- DONE How locking can ensure serialisability.
- Locking achieves serializability by using locks to control access to shared resources (e.g., database objects like tables or rows) and prevent conflicts between concurrent transactions.
- DONE 2PL
- In the 2PL protocol, transactions acquire and release locks on database objects (e.g., tables, rows) in two distinct phases: the growing phase and the shrinking phase.
- DONE Deadlock and how it can be resolved.
- A deadlock is a situation in which two or more transactions are unable to proceed because each is waiting for a resource held by the other, resulting in a circular dependency and a system halt. It is a form of resource contention that can occur in concurrent systems, including database management systems.
- DONE How timestamping can ensure serialisability.
- By using transaction timestamps and enforcing the read and write validation checks, concurrency control mechanisms can ensure that transactions are executed in a way that maintains data consistency and serializability.
- DONE Recovery Control
- DONE Some causes of database failure.
- System crashes, resulting in loss of main memory.
- Power failures
- Disk crashes, resulting in loss of parts of secondary storage.
- Application software errors.
- Natural physical disasters.
- User mistakes.
- Sabotage.
- DONE Purpose of transaction log file.
- Contains information about all updates to
database:
- Transaction records.
- Checkpoint records.
- Often used for other purposes (for example, auditing).
- For autiding
- Contains information about all updates to
database:
- DONE Purpose of checkpointing.
- When failure occurs, redo all transactions that committed since the checkpoint and undo all transactions active at time of crash.
- DONE Some causes of database failure.
- DONE ACID (Atomicity, Consistency, Isolation, Durability): A set of properties that guarantee the reliability and integrity of database transactions.
- DONE Normalization
background-color:: yellow
- DONE Functional dependencies g4g
- In a relational database management, functional dependency is a concept that specifies the relationship between two sets of attributes where one attribute determines the value of another attribute. It is denoted as X → Y, where the attribute set on the left side of the arrow, X is called Determinant , and Y is called the Dependent.
- DONE BCNF vs. 3NF :LOGBOOK: CLOCK: [2023-06-01 Thu 17:38:55]--[2023-06-01 Thu 17:38:56] => 00:00:01 :END:
- DONE kinds of NF tutorial
- First Normal Form (1NF): This is the most basic level of normalization. In 1NF, each table cell should contain only a single value, and each column should have a unique name. The first normal form helps to eliminate duplicate data and simplify queries.
- Second Normal Form (2NF): 2NF eliminates redundant data by requiring that each non-key attribute be dependent on the primary key. This means that each column should be directly related to the primary key, and not to other columns.
- Third Normal Form (3NF): 3NF builds on 2NF by requiring that all non-key attributes are independent of each other. This means that each column should be directly related to the primary key, and not to any other columns in the same table.
- Boyce-Codd Normal Form (BCNF): BCNF is a stricter form of 3NF that ensures that each determinant in a table is a candidate key. In other words, BCNF ensures that each non-key attribute is dependent only on the candidate key.
- Fourth Normal Form (4NF): 4NF is a further refinement of BCNF that ensures that a table does not contain any multi-valued dependencies.
- Fifth Normal Form (5NF): 5NF is the highest level of normalization and involves decomposing a table into smaller tables to remove data redundancy and improve data integrity.
- DONE Functional dependencies g4g
- DONE DB transaction management
- DONE Block 4
- DONE Distributed DBMS
collapsed:: true
- DONE client server arch
collapsed:: true
- Computers (client) connected over wired or wireless local area network (LAN)
- The database itself and the DBMS are stored on a central device called the database server, which is also connected to the network.
- Distributed Database
collapsed:: true
- A logically interrelated collection of shared data (and a description of this data), physically spread over a computer network.
- Distributed DBMS
collapsed:: true
- Software system that permits the management of the distributed database and makes the distribution transparent to users.
- the key issues
collapsed:: true
- Fragmentation
- Allocation
- Replication
- importance and different types of fragmentation
collapsed:: true
- Horizontal
- Vertical
- Mixed
- different types of transparency
collapsed:: true
- Distribution Transparency: The database feels as a single, logical entity
- Transaction Transparency: Ensures that all distributed transactions maintain distributed database’s integrity and consistency.
- Performance Transparency: must perform as if it were a centralized DBMS.
- advantages and disadvantages of distributed databases
- DONE client server arch
collapsed:: true
- DONE XML
collapsed:: true
- XML definition and basic concepts
collapsed:: true
- eXtensible Markup Language
- A meta-language (i.e. a language for describing other languages) that enables designers to create their own customised tags to provide functionality not available with HTML.
- Relational model versus XML
collapsed:: true
- SQL
collapsed:: true
- is a special-purpose programming language
- You can: manage data in a relational databases.
- XML
collapsed:: true
- is a markup specification language
- You can: design ways of describing information (text or data), usually for storage, transmission, or processing by a program (you can use it in combination with a programming language).
- It says nothing about what you should do with the data (although your choice of element names may hint at what they are for).
- SQL
collapsed:: true
- Well-formed XML, Valid XML
collapsed:: true
- Adheres to basic structural requirements - Single root element
- Matched tags, proper nesting
- Unique attributes within elements
- DTD, XSD
collapsed:: true
- DTD: Defines the valid syntax of an XML document
- XSD: a more comprehensive method of defining content model of an XML document.
- XML definition and basic concepts
collapsed:: true
- DONE Data Mining
collapsed:: true
- concept
collapsed:: true
- The process of extracting valid, previously unknown, comprehensible, and actionable information from large databases and using it to make crucial business decisions.
- different applications
collapsed:: true
- Retail / Marketing
- Banking
- Insurance
- Medicine
- basic techniques
collapsed:: true
- predictive modelling,
collapsed:: true
- uses observations to form a model of the important characteristics of some phenomenon
- database segmentation,
collapsed:: true
- Uses unsupervised learning to discover homogeneous subpopulations in a database to improve the accuracy of the profiles.
- link analysis,
collapsed:: true
- Establishing links, called associations, between the individual records, or sets of records, in a database.
- deviation detection.
collapsed:: true
- Identifies outliers, which express deviation from some previously known expectation and norm.
- predictive modelling,
collapsed:: true
- concept
collapsed:: true
- DONE NoSQL
collapsed:: true
- the motivation for NoSQL
collapsed:: true
- By giving up ACID constraints, one can achieve much higher performance and scalability.
- explain the concepts of NoSQL
collapsed:: true
- NoSQL databases (aka "not only SQL") are non-tabular databases and store data differently than relational tables. NoSQL databases come in a variety of types based on their data model. The main types are document, key-value, wide-column, and graph. They provide flexible schemas and scale easily with large amounts of data and high user loads.
- explain the application areas of NoSQL
collapsed:: true
- NoSQL is an alternative, non-traditional DB technology to be used in large scale environments where (ACID) transactions are not a priority.
- CAP theorem:
collapsed:: true
- There are 3 main properties for distributed management:
- Consistency → A data item has the same value at the same time (to ensure coherency).
- Availability → Data is available, even if a server is down.
- Partition Tolerance → A query must have an answer, even if the system is partitioned (unless there is a global failure).
- There are 3 main properties for distributed management:
- the motivation for NoSQL
collapsed:: true
- DONE Distributed DBMS
collapsed:: true
- DONE Terms in: chatGPT
- LATER Block 1
- LATER Exercises
- LATER past year exercise 1
- LATER past year exercise 2
- LATER past year exercise 3
- DONE 课件
collapsed:: true
:LOGBOOK:
CLOCK: [2023-06-01 Thu 17:01:28]--[2023-06-01 Thu 17:01:30] => 00:00:02
CLOCK: [2023-06-01 Thu 17:01:41]--[2023-06-01 Thu 17:38:19] => 00:36:38
:END:
- LATER 产品开发 {{renderer :todomaster}}
collapsed:: true
SCHEDULED: <2023-06-16 Fri>
- DONE 整理考点 :LOGBOOK: CLOCK: [2023-06-09 Fri 15:05:10]--[2023-06-09 Fri 15:05:11] => 00:00:01 :END:
- LATER See past exam papers
- LATER 整理 ppt
- DONE Week 1
- {{embed ((648581e7-cc5c-4514-9c2a-0b6af4adc5bb))}}
- {{embed ((648594af-3833-4991-a4c2-2e9c8430a122))}}
- Topic 4: Product Planning
- {{embed ((64859157-dc41-453d-95ea-39e2280ea735))}}
- DONE Week 2
- {{embed ((6482bafb-b96b-44c3-834b-8b4966c1dc0c))}}
- {{embed ((64857305-2925-485f-9aed-e15511b42149))}}
- {{embed ((64857305-a186-4927-890d-607f66d97f95))}}
- DONE Week 3
- DONE Week4
- DONE Week 1
- LATER 概率论 (隔了一个周末)
collapsed:: true
SCHEDULED: <2023-06-19 Mon>
- {{embed ((647bf024-41f1-45e7-afaf-f49026e826d6))}}
- DONE Java {{renderer :todomaster}}
collapsed:: true
SCHEDULED: <2023-06-12 Mon>
:LOGBOOK:
CLOCK: [2023-06-09 Fri 15:09:23]--[2023-06-09 Fri 16:26:51] => 01:17:28
:END: