11 KiB
11 KiB
SLA and Virtualization
SLA
Definition
- Service Level Agreement: a service-based legal agreement between a provider and a subscriber
- Accepted before a cloud service can be used
- Content
- Provider's responsibility
- Subscriber's responsibility, and entitlements
- Billing and accounting system
Types
- Service based SLA:
- Offer shared resources, used by many customers
- Offered to cloud users
- Customer based SLA
- Agreement between individual customer or group, to provide non-shared specific services
- Multi-level SLA:
- Corporate level: generic and cover all user of an organization
- Customer level: specific group of user
- Service: specific type of service
Boundaries
- Organizational boundary
- Physical perimeter, owned and governed by organization or cloud provider
- Trust boundary
- When cloud user extend trust beyond its physical boundary, and include resources from the cloud
Characteristics of cloud
- On-demand usage: use more cloud resources only when they need it
- Multi-tenancy aka. Resource pooling: Resources are instances that can be used by many users
- Scalability: Able to automatically scale up or down based on the settings and agreements
- Ubiquitous access: Can be accessed everywhere with lots of devices
- Measured usage: keep track and record the amount of IT resources used by
consumers
- Used for accounting and auditing
- Resilience: distribute and replicate resources to provide redundancy, and fail over mechanism
QoS
- SLA is based on Quality of Service
- Combination of metrics relating to requirements, and satisfaction of services offered by a provider.
- Quantitative or qualitative
- Parameters:
- Reliability availability
- Security and trust
- Scalability
- Data integrity and data protection
- Resilience
- Data recovery time
- Support
Virtualization
Definition
- The process of creating the virtual version of hardware, database, operating system and application from real copies, using virtual machine monitor to emulate the physical functionalities.
- Multiple virtual machines are multiplexed in to the same hardware, to serve as an abstraction of physical OS
- Guest OS is not bound to the physical hardware.
- Guest OS runs on host OS, and they can be different
Levels of virtualization
- Instruction Set Architecture level: ISA emulation, which is used to run many legacy codes written for a different hardware configuration, like Dynamo
- Hardware level: VMs are located directly on top of hardware, allows the virtualization of each of the hardware components, which could be the input-output device, the memory, the processor, etc, like VMWare
- Operating system level: an operating system (OS) virtualization paradigm in which the kernel allows the existence of multiple isolated user space instances, like Jails
- Library level: translate API calls to user libraries, like vCUDA
- Application level: allows high-level language programs to be compiled easily. java's jvm
Types of Virtualizations
- Desktop: Create desktop computer from physical desktop machine
- Hardware: Virtual computer with OS that represents and act as a real physical computer.
- Nested virtualization: Virtual machine inside another one
- CPU virtualization: Virtual CPU are created to reduce stress on host
- Memory virtualization: virtual memory is created and run on the VM, controlled by the virtual CPU of VM, but can't access memory address outside virtual
- IO virtualization: Route IO request between virtual devices and physical hardware
Virtual clusters
- Physical cluster: interconnected by physical network
- Failure may cause a falling physical node
- Virtual cluster: VMs intereconnected by a virtual network across several
physical networks
- Node can be either physical or virtual
- Cluster VMs can run different OS
- To enhance utilization and flexibility
- Can be freely replicated, and is fault tolerant easy to recover
- Nodes can grow or shrink
- Failure won't cause shutdown to host machine
Migration of VM
Introduction
- VM can be moved from one cluster to another, which isn't possible with physical hosts.
- Four ways:
- Guest-based manager, where cluster manager is in guest vm
- Host based manager: supervises the guest system, and can restart guest system remotely
- Independent cluster manager on both host and guest
- Use integrated cluster manager
Six (five) steps of VM migration
- Start migration (for some reason this is counted as step 0 and 1???)
- Determine VM to migrate
- Determine destination host
- Transfer memory
- State is stored in memory, so transfer memory first
- Suspend VM and copy remaining data
- Execution is suspended when last memory is transfered.
- Non memory components like network and cpu are sent to destination
- Commit
- After all data, VM reloads and continue execution
- Activate
- Network is redirected to new VM
- remove the original VM from source host
Mechanism for cloud infra: building blocks
- Environment:
- Logical network perimeter: Virtual network boundary, encompass and isolate a group of resources, that may be physically distributed., to isolate cloud resource from unauthorized users
- Virtual Server: behaves exactly like a physical one, and running on the same physical server which is shared by multiple cloud users
- Resource replication: create multiple of same resource to various locations, physically distributed around the world.
- Ready made environment: provided by PaaS (platform as a service)
- Failover system: use clustering to provide redundancy
- Hypervisor: generate virtual server instances
- Multi device broker: converts and exchanges information
- Resource cluster: cloud resources are geographically distributed and group resources and instances together
- State management database, used to temporarily maintain state data for software programs to improve performance.
- Scaling
- Automated Scaling listener: monitors communication between consumers and services for dynamic scaling up or down.
- Load balancer: cloud runtime mechanism that distributes workload: data processing, computation, network traffic across two or more cloud resources, for better performance( automated horizontal scaling)
- Monitoring
- Cloud usage monitor: Autonomous software used for collecting and processing cloud resource usage data.
- SLA monitor: monitors the performance to ensure they are fulfilling the Quality of Service requirement
- Pay per use monitor: monitor the usage and calculate the price according to the agreement
- Audit monitor: track data for network, to confirm to regulatory obligation
Different hypervisors
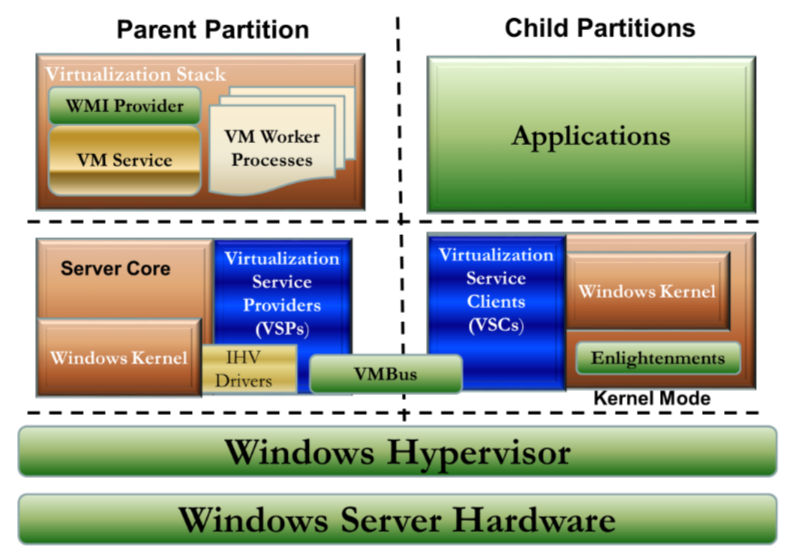
Microsoft virtualization technology
- parent partition: logical hard drive for running hypervisor layer, and nesting child partitions
- Child partitions: Logical hard drive responsible for running isolated OSes
- Virtualization stack Collections of resources including the hypervisor, which makes up the Microsoft hyper V
- Virtualization service provider: parent partition side, server that handles IO
- Virtualization child provider: child partition component, that sends request to VSP
- VMBus: send requests and data between VMs
- WMI: Windows management instrumentation, manages virtual devices
- Windows kernel: manages IO request from parent and child
- IHV: hardware drivers
- VM worker process: run and configure one VM each
- Hypervisor
- Manages a minimum set of hardware components
- Isolate component, to enhance loose coupling
- Provide security
- Enhance performance
Xen Virtualization Technology
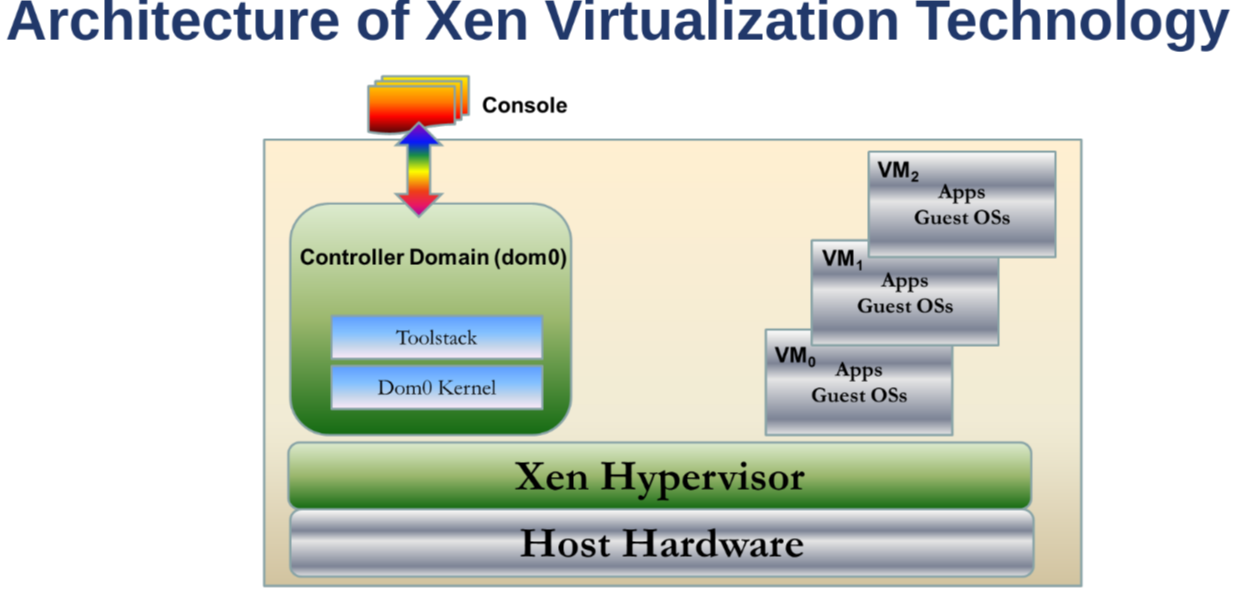
- Host Hardware: real hardware
- Xen Hypervisor: lean software layer, that runs on host hardware and manages the CPUs, memory, IO devices
- Guest Domains / Virtual Machines
- Control Domain, or domain 0: special virtual machine with privilege to access, and handles IO functions and VM's interactions
- Toolstack: control stack on domain 0, enables user to manage virtual machines
Virtualization Technologies
- host components: real hardware
- guest components: virtual system created from host machine, includes os, network, databases and servers
- Hypervisor, or virtual machine manager: manages virtual machines
- Networking technologies
- Web services: manager over the internet
- Front end systems: interface between user and virtual machine
Advantages and challenges
Advantages:
- Deployment:
- Less cost, reduction in cost of hardware, energy, cooling , expertise and administration
- Less time needed
- Creating servers on different system is easy
- Maintainence:
- Scalability
- Efficiency
- Reliability
- Fast data disaster recovery
- Backups and migrations are easy
Challenges
- Security of virtual machines
- Need expertise to manage virtual machines
- Reliant back up systems are needed
- Failures of host will affect the guest system.
- Performance may not be as good as using physical ones
Future of Virtualization
- Is and will be the dominant component of cloud computing
- Decoupling of application will increase
- Less energy consumption by optimizing OS and VMM
- Dominant in IT market
- Even more scalable
- Better security
Major classes of hardware virtualization
Full virtualization, Hardware virtual machine
- Complete simulation of actual hardware, so that OS and software doesn't need any modifications.
- AWS Support
- HVM AMI (Amazon Machine Images), in a fully virtualized environment
- Can run OS without modification
- HW extension is support
- Instance type support: all current
- Regioin: all
Paravirtualization
- Allows guest applications to be executed, as if they are running on a separate system, but hard ware environment is not simulated
- Guest need to be modified
- AWS Support
- PV AMI: special bootloader is used
- Can run on host hardware without explicit support for virtualization
- Hardware extention is not supported
- Some instance types are supported
- Some regions are supported
Layering and Virtualization
Layering
- Definition: approach to manage system complexity
- Goals:
- Simplify description of subsystem, to abstract through interface
- Minimize interaction between subsystems
- Enable us to independently manage each subsystem
- Layering in computers:
- Hardware
- Software
- OS
- Library
- Applications
Interfaces in virtualization
- ISA (Instruction Set Architecture): Instruction Set Architecture: boundary between hardware and software
- ABI (Application Binary Interface): Allow application and library modules to access hardware, invokes system calls
- API (Application Program Interface): Is a set of rules or protocols that enables software applications to communicate with each other to exchange data, features and functionality